Cryptographic Authentication & Authorization Methods for the Web using Blockchain Technologies
In this solo research work, I investigated password-less authentication and authorization methods for the web. My method utilized traditional public key cryptography to register and login users to protected websites. The technique I developed bootstrapped itself off of popular browser-based signing authorities like Metamask.
The cryptographic authentication methods I developed store user claims encrypted on the blockchain, using the user's public key. This allows users to directly query, decrypt, and verify the claims that the service has granted them. This completely eliminates the common data security pitfalls inherent in password-based authentication. When logging in to protected services, users submit a signature using their key-pair. Thereafter the service verifies this signature against the stored claims object and if successful, grants access to the protected content.
The report is concise and accessible to a wide audience. It can be read here.
Tech Stack
Overview
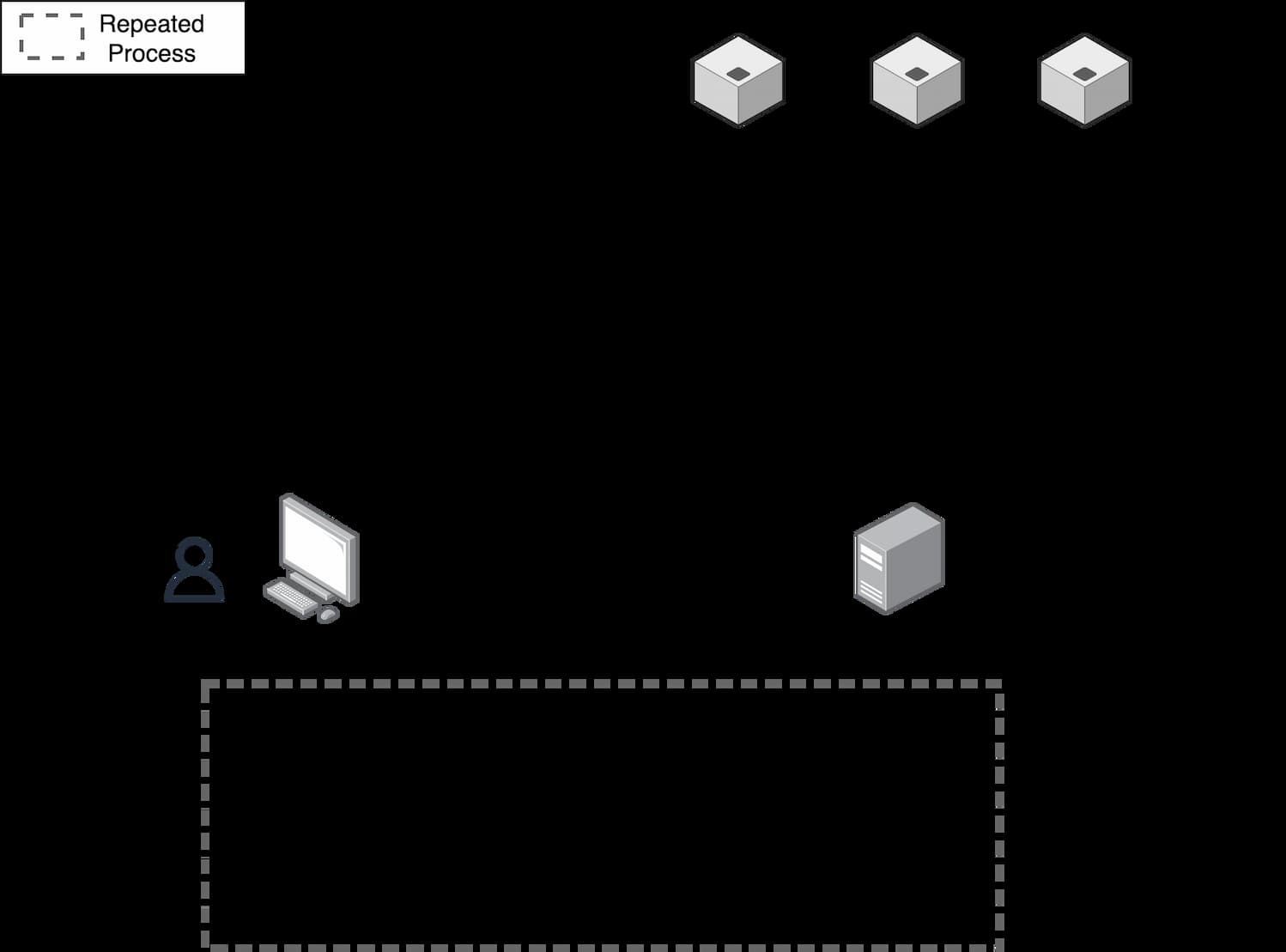
Architecture
The process for registering and subsequently logging-in a user works in the following way:
- The user registers with the service by submitting the requested data and signing the payload.
- Thereafter the service encrypts this data using the user's public key and stores it on the blockchain. This encrypted data forms the user's claim.
- The user can retrieve, decrypt, and verify the signature on the submitted data to validate the integrity of the claim.
- When the user goes to log in, they submit a signed message of their address. The service can then verify this signature, match it with the data stored on chain, and verify the claim. According to service specific business logic, it can now grant access to the protected content.
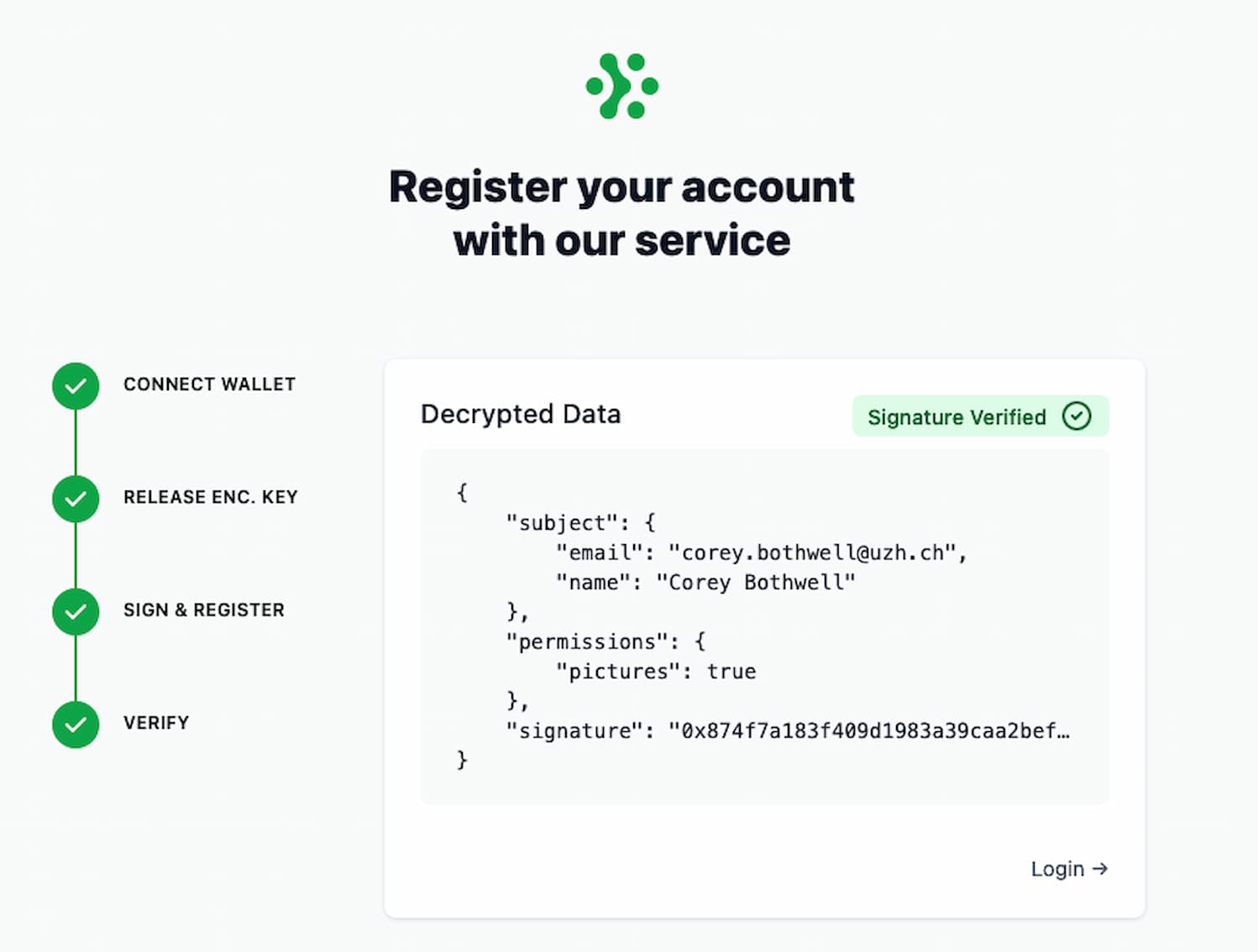
Validating the Signature
Validating the signature allows the user to verify the integrity of the stored claim.
The Protected Content
When logging in, users submit a signed message of their address. Upon matching against the stored claim, the service can selectively grant access to the protected content.

My Responsibilities
I was sole author of the developed techniques, accompanying codebase, and associated paper.